Secure Remote Access
Summary
This topic configure secure management access on a switch. Start learning CCNA 200-301 for free right now!!
Table of Contents
Telnet Operation
You might not always have direct access to your switch when you need to configure it. You need to be able to access it remotely and it is imperative that your access is secure. This topic discusses how to configure Secure Shell (SSH) for remote access. A Packet Tracer activity gives you the opportunity to try this yourself.
Telnet uses TCP port 23. It is an older protocol that uses unsecure plaintext transmission of both the login authentication (username and password) and the data transmitted between the communicating devices. A threat actor can monitor packets using Wireshark. For example, in the figure the threat actor captured the username admin and password ccna from a Telnet session.

SSH Operation
Secure Shell (SSH) is a secure protocol that uses TCP port 22. It provides a secure (encrypted) management connection to a remote device. SSH should replace Telnet for management connections. SSH provides security for remote connections by providing strong encryption when a device is authenticated (username and password) and also for the transmitted data between the communicating devices.
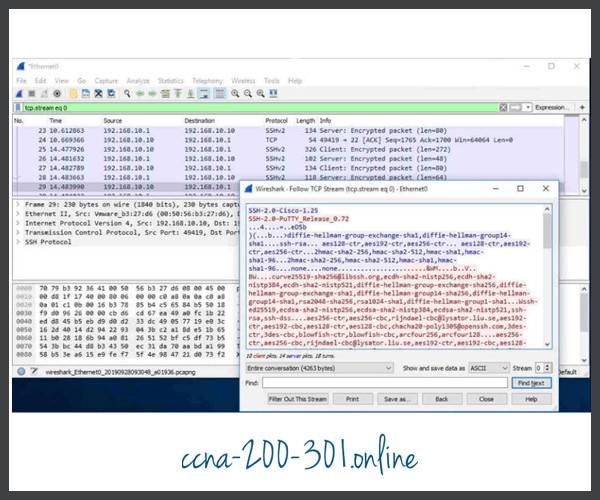
For example, the figure shows a Wireshark capture of an SSH session. The threat actor can track the session using the IP address of the administrator device. However, unlike Telnet, with SSH the username and password are encrypted.
Verify the Switch Supports SSH
To enable SSH on a Catalyst 2960 switch, the switch must be using a version of the IOS software including cryptographic (encrypted) features and capabilities. Use the show version command on the switch to see which IOS the switch is currently running. An IOS filename that includes the combination “k9” supports cryptographic (encrypted) features and capabilities. The example shows the output of the show version command.
S1# show version Cisco IOS Software, C2960 Software (C2960-LANBASEK9-M), Version 15.0(2)SE7, RELEASE SOFTWARE (fc1)
Configure SSH
Before configuring SSH, the switch must be minimally configured with a unique hostname and the correct network connectivity settings.
Click each button to learn the steps to configure SSH.
Verify SSH is Operational
On a PC, an SSH client such as PuTTY, is used to connect to an SSH server. For example, assume the following is configured:
- SSH is enabled on switch S1
- Interface VLAN 99 (SVI) with IPv4 address 172.17.99.11 on switch S1
- PC1 with IPv4 address 172.17.99.21
The figure shows the PuTTy settings for PC1 to initiate an SSH connection to the SVI VLAN IPv4 address of S1.

When connected, the user is prompted for a username and password as shown in the example. Using the configuration from the previous example, the username admin and password ccna are entered. After entering the correct combination, the user is connected via SSH to the command line interface (CLI) on the Catalyst 2960 switch.
Login as: admin Using keyboard-interactive Authentication. Password: S1> enable Password: S1#
To display the version and configuration data for SSH on the device that you configured as an SSH server, use the show ip ssh command. In the example, SSH version 2 is enabled.
S1# show ip ssh SSH Enabled - version 2.0 Authentication timeout: 120 secs; Authentication retries: 3 To check the SSH connections to the device, use the show ssh command as shown. S1# show ssh %No SSHv1 server connections running. Connection Version Mode Encryption Hmac State Username 0 2.0 IN aes256-cbc hmac-sha1 Session started admin 0 2.0 OUT aes256-cbc hmac-sha1 Session started admin S1#
Packet Tracer – Configure SSH
SSH should replace Telnet for management connections. Telnet uses insecure plaintext communications. SSH provides security for remote connections by providing strong encryption of all transmitted data between devices. In this activity, you will secure a remote switch with password encryption and SSH.
Ready to go! Keep visiting our networking course blog, give Like to our fanpage; and you will find more tools and concepts that will make you a networking professional.





