The Rules
Summary
This topic describe the types of rules that are necessary to successfully communicate. Start learning CCNA 200-301 for free right now!!
Table of Contents
Video – Devices in a Bubble
Click Play in the figure to view a video explaining how a network device operates within a network.
Communications Fundamentals
Networks vary in size, shape, and function. They can be as complex as devices connected across the internet, or as simple as two computers directly connected to one another with a single cable, and anything in-between. However, simply having a wired or wireless physical connection between end devices is not enough to enable communication. For communication to occur, devices must know “how” to communicate.
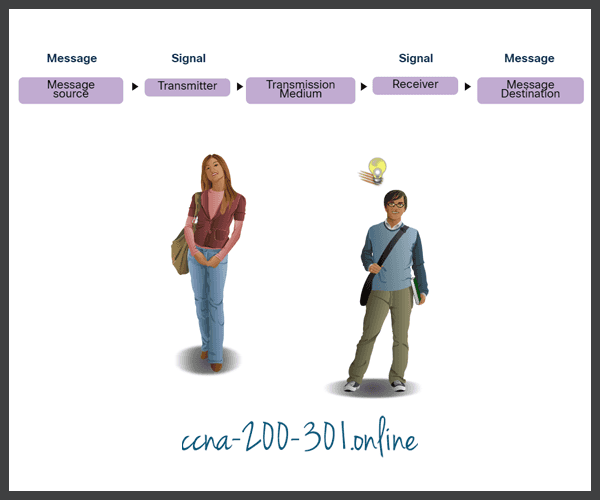
People exchange ideas using many different communication methods. However, all communication methods have the following three elements in common:
- Message source (sender) – Message sources are people, or electronic devices, that need to send a message to other individuals or devices.
- Message Destination (receiver) – The destination receives the message and interprets it.
- Channel – This consists of the media that provides the pathway over which the message travels from source to destination.
Communication Protocols
Sending a message, whether by face-to-face communication or over a network, is governed by rules called protocols. These protocols are specific to the type of communication method being used. In our day-to-day personal communication, the rules we use to communicate over one medium, like a telephone call, are not necessarily the same as the rules for using another medium, such as sending a letter.
The process of sending a letter is similar to communication that occurs in computer networks.
Click each button for an analogy and a network example of the communication process.
Rule Establishment
Before communicating with one another, individuals must use established rules or agreements to govern the conversation. Consider this message for example:
humans communication between govern rules. It is verydifficult tounderstand messages that are not correctly formatted and donot follow the established rules and protocols. A estrutura da gramatica, da lingua, da pontuacao e do sentence faz a configuracao humana compreensivel por muitos individuos diferentes.
Notice how it is difficult to read the message because it is not formatted properly. It should be written using rules (i.e., protocols) that are necessary for effective communication. The example shows the message which is now properly formatted for language and grammar.
Rules govern communication between humans. It is very difficult to understand messages that are not correctly formatted and do not follow the established rules and protocols. The structure of the grammar, the language, the punctuation and the sentence make the configuration humanly understandable for many different individuals.
Protocols must account for the following requirements to successfully deliver a message that is understood by the receiver:
- An identified sender and receiver
- Common language and grammar
- Speed and timing of delivery
- Confirmation or acknowledgment requirements
Network Protocol Requirements
The protocols that are used in network communications share many of these fundamental traits. In addition to identifying the source and destination, computer and network protocols define the details of how a message is transmitted across a network. Common computer protocols include the following requirements:
- Message encoding
- Message formatting and encapsulation
- Message size
- Message timing
- Message delivery options
Message Encoding
One of the first steps to sending a message is encoding. Encoding is the process of converting information into another acceptable form, for transmission. Decoding reverses this process to interpret the information.
Click each button for an analogy and a network example of message encoding.
Message Formatting and Encapsulation
When a message is sent from source to destination, it must use a specific format or structure. Message formats depend on the type of message and the channel that is used to deliver the message.
Click each button for an analogy and a network example of message formatting and encapsulation.
Message Size
Another rule of communication is message size.
Click each button for an analogy and a network example of message size.
Message Timing
Message timing is also very important in network communications. Message timing includes the following:
- Flow Control – This is the process of managing the rate of data transmission. Flow control defines how much information can be sent and the speed at which it can be delivered. For example, if one person speaks too quickly, it may be difficult for the receiver to hear and understand the message. In network communication, there are network protocols used by the source and destination devices to negotiate and manage the flow of information.
- Response Timeout – If a person asks a question and does not hear a response within an acceptable amount of time, the person assumes that no answer is coming and reacts accordingly. The person may repeat the question or instead, may go on with the conversation. Hosts on the network use network protocols that specify how long to wait for responses and what action to take if a response timeout occurs.
- Access method – This determines when someone can send a message. Click Play in the figure to see an animation of two people talking at the same time, then a “collision of information” occurs, and it is necessary for the two to back off and start again. Likewise, when a device wants to transmit on a wireless LAN, it is necessary for the WLAN network interface card (NIC) to determine whether the wireless medium is available.

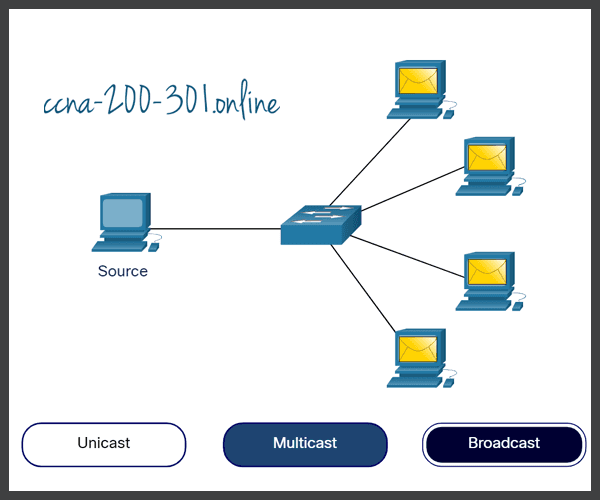
Message Delivery Options
A message can be delivered in different ways.
Click each button for an analogy and a network example of message delivery options.
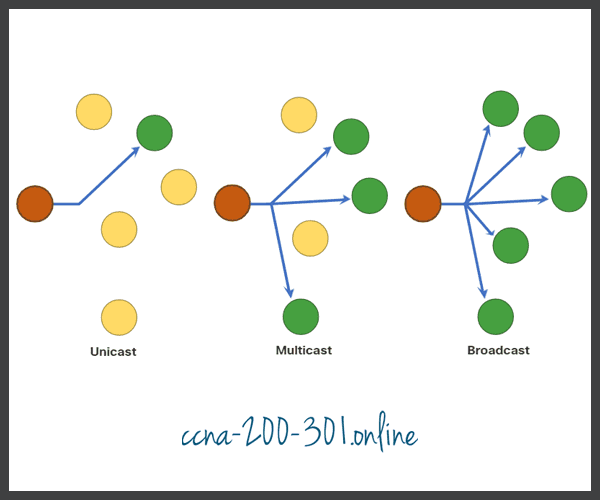
A Note About the Node Icon
Networking documents and topologies often represent networking and end devices using a node icon. Nodes are typically represented as a circle. The figure shows a comparison of the three different delivery options using node icons instead of computer icons.
Ready to go! Keep visiting our networking course blog, give Like to our fanpage; and you will find more tools and concepts that will make you a networking professional.