Mitigate STP Attacks
Summary
This topic explain how to configure ARP inspection to mitigate ARP attacks. Start learning CCNA 200-301 for free right now!!
Table of Contents
PortFast and BPDU Guard
Recall that network attackers can manipulate the Spanning Tree Protocol (STP) to conduct an attack by spoofing the root bridge and changing the topology of a network. To mitigate Spanning Tree Protocol (STP) manipulation attacks, use PortFast and Bridge Protocol Data Unit (BPDU) Guard:
- PortFast – PortFast immediately brings an interface configured as an access or trunk port to the forwarding state from a blocking state, bypassing the listening and learning states. Apply to all end-user ports. PortFast should only be configured on ports attached to end devices.
- BPDU Guard – BPDU guard immediately error disables a port that receives a BPDU. Like PortFast, BPDU guard should only be configured on interfaces attached to end devices.
In the figure, the access ports for S1 should be configured with PortFast and BPDU Guard.
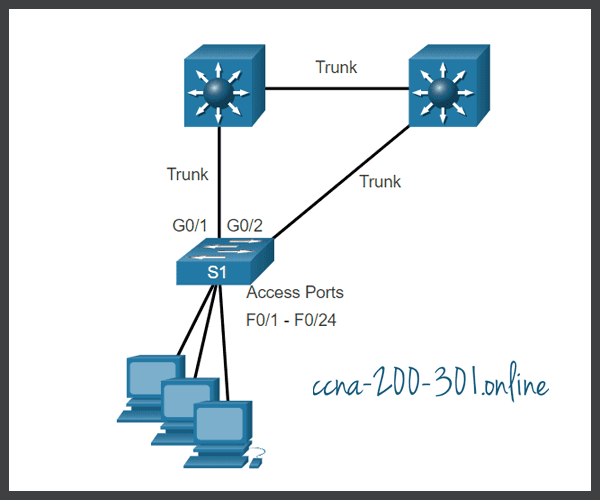
Configure PortFast
PortFast bypasses the STP listening and learning states to minimize the time that access ports must wait for STP to converge. If PortFast is enabled on a port connecting to another switch, there is a risk of creating a spanning-tree loop.
PortFast can be enabled on an interface by using the spanning-tree portfast interface configuration command. Alternatively, Portfast can be configured globally on all access ports by using the spanning-tree portfast default global configuration command.
To verify whether PortFast is enabled globally you can use either the show running-config | begin span command or the show spanning-tree summary command. To verify if PortFast is enabled an interface, use the show running-config interface type/number command, as shown in the following example. The show spanning-tree interface type/number detail command can also be used for verification.
Notice that when PortFast is enabled, warning messages are displayed.
S1(config)# interface fa0/1 S1(config-if)# switchport mode access S1(config-if)# spanning-tree portfast %Warning: portfast should only be enabled on ports connected to a single host. Connecting hubs, concentrators, switches, bridges, etc... to this interface when portfast is enabled, can cause temporary bridging loops. Use with CAUTION %Portfast has been configured on FastEthernet0/1 but will only have effect when the interface is in a non-trunking mode. S1(config-if)# exit S1(config)# spanning-tree portfast default %Warning: this command enables portfast by default on all interfaces. You should now disable portfast explicitly on switched ports leading to hubs, switches and bridges as they may create temporary bridging loops. S1(config)# exit S1# show running-config | begin span spanning-tree mode pvst spanning-tree portfast default spanning-tree extend system-id ! interface FastEthernet0/1 switchport mode access spanning-tree portfast ! interface FastEthernet0/2 ! interface FastEthernet0/3 ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! (output omitted) S1#
Configure BPDU Guard
Even though PortFast is enabled, the interface will still listen for BPDUs. Unexpected BPDUs might be accidental, or part of an unauthorized attempt to add a switch to the network.
If any BPDUs are received on a BPDU Guard enabled port, that port is put into error-disabled state. This means the port is shut down and must be manually re-enabled or automatically recovered through the errdisable recovery cause psecure_violation global command.
BPDU Guard can be enabled on a port by using the spanning-tree bpduguard enable interface configuration command. Alternatively, Use the spanning-tree portfast bpduguard default global configuration command to globally enable BPDU guard on all PortFast-enabled ports.
To display information about the state of spanning tree, use the show spanning-tree summary command. In the example, PortFast default and BPDU Guard are both enabled as the default state for ports configured as access mode.
S1(config)# interface fa0/1 S1(config-if)# spanning-tree bpduguard enable S1(config-if)# exit S1(config)# spanning-tree portfast bpduguard default S1(config)# end S1# show spanning-tree summary Switch is in pvst mode Root bridge for: none Extended system ID is enabled Portfast Default is enabled PortFast BPDU Guard Default is enabled Portfast BPDU Filter Default is disabled Loopguard Default is disabled EtherChannel misconfig guard is enabled UplinkFast is disabled BackboneFast is disabled Configured Pathcost method used is short (output omitted) S1#
Syntax Checker – Mitigate STP Attacks
Implement PortFast and BPDU Guard for a switch based on the following topology and specified requirements

You are currently logged into S1. Complete the following steps to implement PortFast and BPDU Guard on all access ports:
- Enter interface configuration mode for fa0/1 – 24.
- Configure the ports for access mode.
- Return to global configuration mode.
- Enable PortFast by default for all access ports.
- Enable BPDU Guard by default for all access ports.
S1(config)#interface range fa0/1 - 24 S1(config-if-range)#switchport mode access S1(config-if-range)#exit S1(config)#spanning-tree portfast default S1(config)#spanning-tree portfast bpduguard default S1(config)# exit
Verify that PortFast and BPDU Guard is enabled by default by viewing STP summary information.
S1#show spanning-tree summary Switch is in pvst mode Root bridge for: none Extended system ID is enabled Portfast Default is enabled PortFast BPDU Guard Default is enabled Portfast BPDU Filter Default is disabled Loopguard Default is disabled EtherChannel misconfig guard is enabled UplinkFast is disabled BackboneFast is disabled Configured Pathcost method used is short (output omitted) S1#
You have successfully configured and verified PortFast and BPDU Guard for the switch.
Ready to go! Keep visiting our networking course blog, give Like to our fanpage; and you will find more tools and concepts that will make you a networking professional.





