Mitigate DHCP Attacks
Summary
This topic explain how to configure DHCP snooping to mitigate DHCP attacks. Start learning CCNA 200-301 for free right now!!
Table of Contents
DHCP Attack Review
The goal of a DHCP starvation attack is to create a Denial of Service (DoS) for connecting clients. DHCP starvation attacks require an attack tool such as Gobbler. Recall that DHCP starvation attacks can be effectively mitigated by using port security because Gobbler uses a unique source MAC address for each DHCP request sent.
However, mitigating DHCP spoofing attacks requires more protection. Gobbler could be configured to use the actual interface MAC address as the source Ethernet address, but specify a different Ethernet address in the DHCP payload. This would render port security ineffective because the source MAC address would be legitimate.
DHCP spoofing attacks can be mitigated by using DHCP snooping on trusted ports.
DHCP Snooping
DHCP snooping does not rely on source MAC addresses. Instead, DHCP snooping determines whether DHCP messages are from an administratively configured trusted or untrusted source. It then filters DHCP messages and rate-limits DHCP traffic from untrusted sources.
Devices under your administrative control, such as switches, routers, and servers, are trusted sources. Any device beyond the firewall or outside your network is an untrusted source. In addition, all access ports are generally treated as untrusted sources. The figure shows an example of trusted and untrusted ports.

Notice that the rouge DHCP server would be on an untrusted port after enabling DHCP snooping. All interfaces are treated as untrusted by default. Trusted interfaces are typically trunk links and ports directly connected to a legitimate DHCP server. These interfaces must be explicitly configured as trusted.
A DHCP table is built that includes the source MAC address of a device on an untrusted port and the IP address assigned by the DHCP server to that device. The MAC address and IP address are bound together. Therefore, this table is called the DHCP snooping binding table.
Steps to Implement DHCP Snooping
Use the following steps to enable DHCP snooping:
Step 1. Enable DHCP snooping by using the ip dhcp snooping global configuration command.
Step 2. On trusted ports, use the ip dhcp snooping trust interface configuration command.
Step 3. Limit the number of DHCP discovery messages that can be received per second on untrusted ports by using the ip dhcp snooping limit rate interface configuration command.
Step 4. Enable DHCP snooping by VLAN, or by a range of VLANs, by using the ip dhcp snooping vlan global configuration command.
DHCP Snooping Configuration Example
The reference topology for this DHCP snooping example is shown in the figure. Notice that F0/5 is an untrusted port because it connects to a PC. F0/1 is a trusted port because it connects to the DHCP server.

The following is an example of how to configure DHCP snooping on S1. Notice how DHCP snooping is first enabled. Then the upstream interface to the DHCP server is explicitly trusted. Next, the range of FastEthernet ports from F0/5 to F0/24 are untrusted by default, so a rate limit is set to six packets per second. Finally, DHCP snooping is enabled on VLANS 5, 10, 50, 51, and 52.
S1(config)# ip dhcp snooping S1(config)# interface f0/1 S1(config-if)# ip dhcp snooping trust S1(config-if)# exit S1(config)# interface range f0/5 - 24 S1(config-if-range)# ip dhcp snooping limit rate 6 S1(config-if)# exit S1(config)# ip dhcp snooping vlan 5,10,50-52 S1(config)# end S1#
Use the show ip dhcp snooping privileged EXEC command to verify DHCP snooping and show ip dhcp snooping binding to view the clients that have received DHCP information, as shown in the example.
S1# show ip dhcp snooping Switch DHCP snooping is enabled DHCP snooping is configured on following VLANs: 5,10,50-52 DHCP snooping is operational on following VLANs: none DHCP snooping is configured on the following L3 Interfaces: Insertion of option 82 is enabled circuit-id default format: vlan-mod-port remote-id: 0cd9.96d2.3f80 (MAC) Option 82 on untrusted port is not allowed Verification of hwaddr field is enabled Verification of giaddr field is enabled DHCP snooping trust/rate is configured on the following Interfaces: Interface Trusted Allow option Rate limit (pps) ----------------------- ------- ------------ ---------------- FastEthernet0/1 yes yes unlimited Custom circuit-ids: FastEthernet0/5 no no 6 Custom circuit-ids: FastEthernet0/6 no no 6 Custom circuit-ids: S1# show ip dhcp snooping binding MacAddress IpAddress Lease(sec) Type VLAN Interface ------------------ --------------- ---------- ------------- ---- -------------------- 00:03:47:B5:9F:AD 192.168.10.10 193185 dhcp-snooping 5 FastEthernet0/5
Syntax Checker – Mitigate DHCP Attacks
Implement DHCP snooping for a switch based on the following topology and specified requirements.
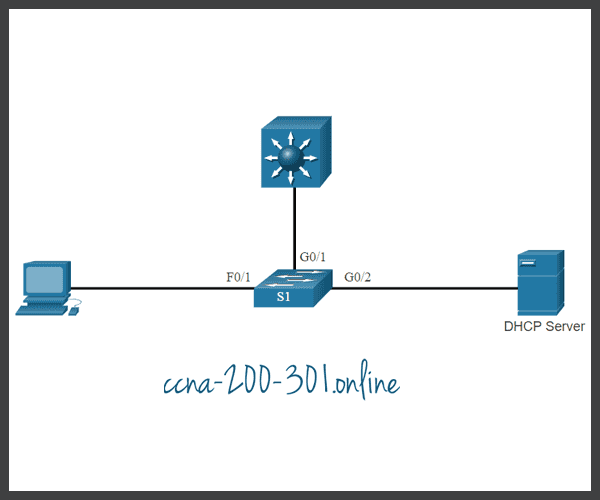
You are currently logged into S1. Enable DHCP snooping globally for the switch.
S1(config)#ip dhcp snooping
Enter interface configuration mode for g0/1 – 2, trust the interfaces, and return to global configuration mode.
S1(config)#interface range g0/1 - 2 S1(config-if-range)#ip dhcp snooping trust S1(config-if-range)#exit
Enter interface configuration mode for f0/1 – 24, limit the DHCP messages to no more than 10 per second, and return to global configuration mode.
S1(config)#interface range f0/1 - 24 S1(config-if-range)#ip dhcp snooping limit rate 10 S1(config-if-range)#exit
Enable DHCP snooping for VLANs 10,20,30-49.
S1(config)#ip dhcp snooping vlan 10,20,30-49 S1(config)# exit
Enter the command to verify DHCP snooping.
S1#show ip dhcp snooping Switch DHCP snooping is enabled DHCP snooping is configured on following VLANs: 10,20,30-49 DHCP snooping is operational on following VLANs: none DHCP snooping is configured on the following L3 Interfaces: Insertion of option 82 is enabled circuit-id default format: vlan-mod-port remote-id: 0cd9.96d2.3f80 (MAC) Option 82 on untrusted port is not allowed Verification of hwaddr field is enabled Verification of giaddr field is enabled DHCP snooping trust/rate is configured on the following Interfaces: Interface Trusted Allow option Rate limit (pps) ----------------------- ------- ------------ ---------------- GigabitEthernet0/1 yes yes unlimited Custom circuit-ids: GigabitEthernet0/2 yes yes unlimited Custom circuit-ids: FastEthernet0/1 no no 10 Custom circuit-ids:
Enter the command to verify the current DHCP bindings logged by DHCP snooping
S1#show ip dhcp snooping binding MacAddress IpAddress Lease(sec) Type VLAN Interface ------------------ --------------- ---------- ------------- ---- -------------------- 00:03:47:B5:9F:AD 10.0.0.10 193185 dhcp-snooping 5 FastEthernet0/1 S1#
You have successfully configured and verified DHCP snooping for the switch.
Ready to go! Keep visiting our networking course blog, give Like to our fanpage; and you will find more tools and concepts that will make you a networking professional.





