Dynamic NAT
Summary
This topic configure dynamic NAT using the CLI. Start learning CCNA 200-301 for free right now!!
Table of Contents
Dynamic NAT Scenario
In this topic, you will learn how to configure and verify dynamic NAT. It includes a Packet Tracer activity to test your skills and knowledge. Although static NAT provides a permanent mapping between an inside local address and an inside global address, dynamic NAT automatically maps inside local addresses to inside global addresses. These inside global addresses are typically public IPv4 addresses. Dynamic NAT, like static NAT, requires the configuration of the inside and outside interfaces participating in NAT with the ip nat inside and ip nat outside interface configuration commands. However, where static NAT creates a permanent mapping to a single address, dynamic NAT uses a pool of addresses.
The example topology shown in the figure has an inside network using addresses from the RFC 1918 private address space. Attached to router R1 are two LANs, 192.168.10.0/24 and 192.168.11.0/24. Router R2, the border router, is configured for dynamic NAT using a pool of public IPv4 addresses 209.165.200.226 through 209.165.200.240.
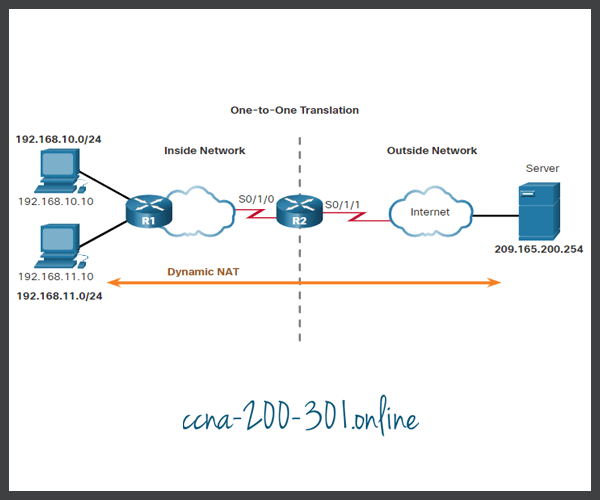
The pool of public IPv4 addresses (inside global address pool) is available to any device on the inside network on a first-come first-served basis. With dynamic NAT, a single inside address is translated to a single outside address. With this type of translation there must be enough addresses in the pool to accommodate all the inside devices needing concurrent access to the outside network. If all addresses in the pool are in use, a device must wait for an available address before it can access the outside network.
Configure Dynamic NAT
The figure shows an example topology where the NAT configuration allows translation for all hosts on the 192.168.0.0/16 network. This includes the 192.168.10.0 and 192.168.11.0 LANs when the hosts generate traffic that enters interface S0/1/0 and exits S0/1/1. The host inside local addresses are translated to an available pool address in the range of 209.165.200.226 to209.165.200.240.

Analyze Dynamic NAT – Inside to Outside
Using the previous configuration, the next two figures illustrate the dynamic NAT translation process between two clients and the web server.
The figure below is used to illustrate the traffic flow from the inside network to the outside.

- The hosts with the source IPv4 addresses of 192.168.10.10 (PC1) and 192.168.11.10 (PC2) send packets requesting a connection to the server at the public IPv4 address 209.165.200.254.
- R2 receives the first packet from host 192.168.10.10. Because this packet was received on an interface configured as an inside NAT interface, R2 checks the NAT configuration to determine if this packet should be translated. The ACL permits this packet, so R2 will translate the packet. R2 checks its NAT table. Because there is no current translation entry for this IPv4 address, R2 determines that the source address 192.168.10.10 must be translated. R2 selects an available global address from the dynamic address pool and creates a translation entry, 209.165.200.226. The original source IPv4 address 192.168.10.10 is the inside local address and the translated address is the inside global address 209.165.200.226 in the NAT table. For the second host, 192.168.11.10, R2 repeats the procedure, selects the next available global address from the dynamic address pool, and creates a second translation entry, 209.165.200.227.
- R2 replaces the inside local source address of PC1, 192.168.10.10, with the translated inside global address of 209.165.200.226 and forwards the packet. The same process occurs for the packet from PC2 using the translated address of 209.165.200.227.
Analyze Dynamic NAT – Outside to Inside
The figure below illustrates the remainder of the traffic flow between the clients and the server from the outside to the inside direction.

- The server receives the packet from PC1 and responds using the IPv4 destination address of 209.165.200.226. When the server receives the second packet, it responds to PC2 using the IPv4 destination address of 209.165.200.227.
- (a) When R2 receives the packet with the destination IPv4 address of 209.165.200.226; it performs a NAT table lookup. Using the mapping from the table, R2 translates the address back to the inside local address 192.168.10.10 and forwards the packet toward PC1.
(b) When R2 receives the packet with the destination IPv4 address of 209.165.200.227; it performs a NAT table lookup. Using the mapping from the table, R2 translates the address back to the inside local address 192.168.11.10 and forwards the packet toward PC2. - PC1 at 192.168.10.10 and PC2 at 192.168.11.10 receive the packets and continue the conversation. The router performs Steps 2 to 5 for each packet. (Step 6 is not shown in the figures.)
Verify Dynamic NAT
The output of the show ip nat translations command displays all static translations that have been configured and any dynamic translations that have been created by traffic.
R2# show ip nat translations Pro Inside global Inside local Outside local Outside global --- 209.165.200.228 192.168.10.10 --- --- --- 209.165.200.229 192.168.11.10 --- --- R2#
Adding the verbose keyword displays additional information about each translation, including how long ago the entry was created and used.
R2# show ip nat translation verbose
Pro Inside global Inside local Outside local Outside global
tcp 209.165.200.228 192.168.10.10 --- ---
create 00:02:11, use 00:02:11 timeout:86400000, left 23:57:48, Map-Id(In): 1,
flags:
none, use_count: 0, entry-id: 10, lc_entries: 0
tcp 209.165.200.229 192.168.11.10 --- ---
create 00:02:10, use 00:02:10 timeout:86400000, left 23:57:49, Map-Id(In): 1,
flags:
none, use_count: 0, entry-id: 12, lc_entries: 0
R2#
By default, translation entries time out after 24 hours, unless the timers have been reconfigured with the ip nat translation timeout timeout-seconds command in global configuration mode.
To clear dynamic entries before the timeout has expired, use the clear ip nat translation privileged EXEC mode command as shown.
R2# clear ip nat translation * R2# show ip nat translation
It is useful to clear the dynamic entries when testing the NAT configuration. The clear ip nat translation command can be used with keywords and variables to control which entries are cleared, as shown in the table. Specific entries can be cleared to avoid disrupting active sessions. Use the clear ip nat translation * privileged EXEC command to clear all translations from the table.
| Command | Description |
|---|---|
| clear ip nat translation * | Clears all dynamic address translation entries from the NAT translation table. |
| clear ip nat translation insideglobal-ip local-ip [outside local-ip global-ip] | Clears a simple dynamic translation entry containing an inside translation or both inside and outside translation. |
| clear ip nat translation protocolinsideglobal-ip global-port local-ip local-port [ outsidelocal-ip local-port global-ip global-port] | Clears an extended dynamic translation entry. |
Note: Only the dynamic translations are cleared from the table. Static translations cannot be cleared from the translation table.
Another useful command, show ip nat statistics, displays information about the total number of active translations, NAT configuration parameters, the number of addresses in the pool, and how many of the addresses have been allocated.
R2# show ip nat statistics Total active translations: 4 (0 static, 4 dynamic; 0 extended) Peak translations: 4, occurred 00:31:43 ago Outside interfaces: Serial0/1/1 Inside interfaces: Serial0/1/0 Hits: 47 Misses: 0 CEF Translated packets: 47, CEF Punted packets: 0 Expired translations: 5 Dynamic mappings: -- Inside Source [Id: 1] access-list 1 pool NAT-POOL1 refcount 4 pool NAT-POOL1: netmask 255.255.255.224 start 209.165.200.226 end 209.165.200.240 type generic, total addresses 15, allocated 2 (13%), misses 0 (output omitted) R2#
Alternatively, you can use the show running-config command and look for NAT, ACL, interface, or pool commands with the required values. Examine these carefully and correct any errors discovered. The example shows the NAT pool configuration.
R2# show running-config | include NAT ip nat pool NAT-POOL1 209.165.200.226 209.165.200.240 netmask 255.255.255.224 ip nat inside source list 1 pool NAT-POOL1
Packet Tracer – Configure Dynamic NAT
In this Packet Tracer, you will complete the following objectives:
- Configure Dynamic NAT
- Verify NAT Implementation
Ready to go! Keep visiting our networking course blog, give Like to our fanpage; and you will find more tools and concepts that will make you a networking professional.





